If you are working in the field of computer networks or an enthusiast in the field of network security, you are sure to have come across the term “Denial of Service attack” which is simply referred to as “DoS attack”. Today, this is one of the most common types of network attacks carried out on the Internet. In this post, I will try to explain DoS attack, its variants and methods involved to carry out the same in an easily understandable manner.
What is a DOS Attack?
Denial of Service or DoS attack is a type of network attack designed to flood the target network or machine with a large amount of useless traffic so as to overload it and eventually bring it down to its knees. The main intention behind DoS attack is to make the services running on the target machine (such as a website) temporarily unavailable to its intended users. DoS attacks are usually carried out on web servers that host vital services such as banking, e-commerce or credit card processing.
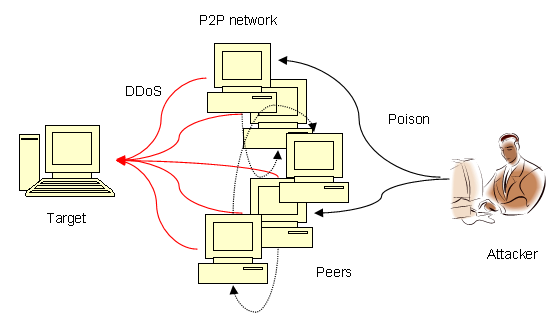
A common variant of DOS attack known as DDoS (Distributed Denial of Service) attack has become quite popular in the recent days as it is more powerful and hard to detect. A typical DoS attack has a single place of origin while a DDoS attack originates from multiple IP addresses distributed across two or more different network. The working of a DDoS attack is shown in the following diagram:
Unlike a DoS attack where the attacker uses one single computer or a network to attack the target, a DDoS the attack originates from different pre-compromised computers belonging to different networks. As the attacker uses a number of computer systems from different networks each residing in different geographical locations, the incoming traffic looks natural and therefore becomes hard to detect.
Protection Against DoS/DDoS Attacks:
DoS attacks can easily be handled by blacklisting the target IP (or range of IPs) that are found to be making too many requests/connections (in an unnatural way) to the server. However, DDoS attacks are complicated as the incoming requests seem more natural and distributed. In this case it is hard to find the difference between the genuine and malicious traffic. Taking an action at the firewall level to blacklist suspected IPs may result in false positives and therefore may affect the genuine traffic as well.
How to defend against a sync flood attack:
What are some ways to protect against sync flood attacks?A Sync flood attack, better known as a SYN attack, has its origins as one of the original types of distributed denial-of-service (DDoS) attacks and have not been significant threats to enterprises today. Most CERT advice from 1996 still applies to modern systems, but obviously many improvements have been made in the last 15 years.
A SYN attack is one where an attacker makes an initial connection to a victim computer and the victim computer waits for the completion of the connection. The attack is exploiting part of the three-way handshake in TCP for establishing reliable connections. When the initial connection is left open, it consumes resources on the victim computer until it runs out of connections or has other issues.
To protect against sync flood attacks, you have several options. The attacks can be detected by standard intrusion detection systems (IDS) and could also be blocked or minimized by built-in features in firewalls and other devices. Further protections could include lowering timeouts for how long a system waits for another system to complete the three-way handshake or having your ISP block the attacks.
Methods Involved in DoS Attack
The following are some of the commonly employed methods in carrying out a DoS attack:
- SYN Flood Attack
- Ping Flood Attack (Ping of Death)
- Teardrop Attack
- Peer-to-Peer Attacks
1. SYN Flood Attack
The attack involves having a client repeatedly send SYN (synchronization) packets to every port on a server, using fake IP addresses. When an attack begins, the server sees the equivalent of multiple attempts to establish communications. The server responds to each attempt with a SYN/ACK (synchronization acknowledged) packet from each open port, and with a RST (reset) packet from each closed port.
In a normal three-way handshake, the client would return an ACK (acknowledged) packet to confirm that the server's SYN/ACK packet was received, and communications would then commence. However, in a SYN flood, the ACK packet is never sent back by the hostile client. Instead, the client program sends repeated SYN requests to all the server's ports. A hostile client always knows a port is open when the server responds with a SYN/ACK packet.
The hostile client makes the SYN requests all appear valid, but because the IP addresses are fake ones, it is impossible for the server to close down the connection by sending RST packets back to the client. Instead, the connection stays open. Before time-out can occur, another SYN packet arrives from the hostile client. A connection of this type is called a half-open connection. Under these conditions, the server becomes completely or almost completely busy with the hostile client and communications with legitimate clients is difficult or impossible. For this reason, SYN floods are also known as half-open attacks.
The transmission by a hostile client of SYN packets for the purpose of finding open ports and hacking into one or more of them, is called SYN scanning.
2. Ping Flood Attack (Ping of Death)
Ping of Death (a.k.a. PoD) is a type of Denial of Service (DoS) attack in which an attacker attempts to crash, destabilize, or freeze the targeted computer or service by sending malformed or oversized packets using a simple ping command.
While PoD attacks exploit legacy weaknesses which may have been patched in target systems. However, in an unpatched systems, the attack is still relevant and dangerous. Recently, a new type of PoD attack has become popular. This attack, commonly known as a Ping flood, the targeted system is hit with ICMP packets sent rapidly via ping without waiting for replies.
Attack Description
The size of a correctly-formed IPv4 packet including the IP header is 65,535 bytes, including a total payload size of 84 bytes. Many historical computer systems simply could not handle larger packets, and would crash if they received one. This bug was easily exploited in early TCP/IP implementations in a wide range of operating systems including Windows, Mac, Unix, Linux, as well as network devices like printers and routers.
Since sending a ping packet larger than 65,535 bytes violates the Internet Protocol, attackers would generally send malformed packets in fragments. When the target system attempts to reassemble the fragments and ends up with an oversized packet, memory overflow could occur and lead to various system problems including crash.
Ping of Death attacks were particularly effective because the attacker’s identity could be easily spoofed. Moreover, a Ping of Death attacker would need no detailed knowledge of the machine he/she was attacking, except for its IP address.
It is worthy of note that this vulnerability, though best recognized for its exploitation by PoD attacks, can actually be exploited by anything that sends an IP datagram - ICMP echo, TCP, UDP and IPX.
Methods of Mitigation
To avoid Ping of Deatch attacks, and its variants, many sites block ICMP ping messages altogether at their firewalls. However, this approach is not viable in the long term.Firstly, invalid packet attacks can be directed at any listening port—like FTP ports—and you may not want to block all of these, for operational reasons.
Moreover, by blocking ping messages, you prevent legitimate ping use – and there are still utilities that rely on ping for checking that connections are live, for example.Incapsula mitigates a massive HTTP flood: 690,000,000 DDoS requests from 180,000 botnets IPs.
The smarter approach would be to selectively block fragmented pings, allowing actual ping traffic to pass through unhindered.
Incapsula DDoS Protection services intelligently and preemptively identify and filter out all abnormally large packets, even if they are fragmented—eliminating the threat of PoD and similar packet-based attacks altogether.
3. Teardrop Attack
A teardrop attack is a denial-of-service (DoS) attack that involves sending fragmented packets to a target machine. Since the machine receiving such packets cannot reassemble them due to a bug in TCP/IP fragmentation reassembly, the packets overlap one another, crashing the target network device. This generally happens on older operating systems such as Windows 3.1x, Windows 95, Windows NT and versions of the Linux kernel prior to 2.1.63.
One of the fields in an IP header is the “fragment offset” field, indicating the starting position, or offset, of the data contained in a fragmented packet relative to the data in the original packet. If the sum of the offset and size of one fragmented packet differs from that of the next fragmented packet, the packets overlap. When this happens, a server vulnerable to teardrop attacks is unable to reassemble the packets - resulting in a denial-of-service condition.
Definition - What does Teardrop Attack mean?
A teardrop attack is a denial of service (DoS) attack conducted by targeting TCP/IP fragmentation reassembly codes. This attack causes fragmented packets to overlap one another on the host receipt; the host attempts to reconstruct them during the process but fails. Gigantic payloads are sent to the machine that is being targeted, causing system crashes.
Techopedia explains Teardrop Attack
While much more popular on older versions of Windows, the teardrop attack is also possible on Windows 7 and Windows Vista machines that have SMB enabled. The driver vulnerability on the latter two operating systems was noted in 2009, but Windows 2000 and Windows XP are not vulnerable to this type of teardrop attack, which hones in on TCP ports 139 and 445 on the firewalls of the SMB-enabled machines. If users don’t have patches to protect against this DoS attack, SMBv2 should be disabled, as recommended by Microsoft, and ports 139 and 445 should be blocked.
4. Peer-to-Peer Attacks
The evolution of computing continues to lead to greater decentralization. Mainframes gave way to local area networks (LANS), which provided greater economies of scale. The Internet has allowed for even greater distribution capability; peer to peer computing has grown as a result. Examples of peer to peer networks include the popular Kazaa and Napster file sharing services. These types of networks allow for significant transfers of data, yet they are vulnerable to attack from multiple sources.
Definition
Peer relationship exploitation can be defined in several ways. First, it can be the exploitation of transitive trust relationships created by peer-networking so as to expand privileges to the transitive closure of peer trust. It can also be defined in less technical terms. Exploitation can be when an insider uses the security access of colleagues to gain access to unauthorized information. This can include physical access or information access. This essay will focus on the first type of attack.
Recommended Articles To Become A Hacker:
How To Become A Hacker - Basic Guide For Beginners 2015
Understand The Hacker Mindset To Become A Real Hacker
Programming Languages For Hackers And Learn It From Most 6 Helpful Websites
Installing Hacker's OS Kali Linux In VMware (Beginners Guide With Screenshots)
Easy Steps to Create Web Penetration Testing Lab in Kali Linux
Introduction to using Metasploit in Kali Linux
An Introduction To Hacker’s OS: Kali Linux And Setup Tutorial.
Linux Powerful Distros For Hacking Or Security: Kali, Tails And Qubes
Become A Hacker: What Is Denial of Service (DoS) Attack?