What is Raspberry Pi?
The Raspberry Pi is a low cost, credit-card sized computer that plugs into a computer monitor or TV, and uses a standard keyboard and mouse. It is a capable little device that enables people of all ages to explore computing, and to learn how to program in languages like Scratch and Python. It’s capable of doing everything you’d expect a desktop computer to do, from browsing the internet and playing high-definition video, to making spreadsheets, word-processing, and playing games.
What’s more, the Raspberry Pi has the ability to interact with the outside world, and has been used in a wide array of digital maker projects, from music machines and parent detectors to weather stations and tweeting birdhouses with infra-red cameras. We want to see the Raspberry Pi being used by kids all over the world to learn to program and understand how computers work.
Installing Kali Linux 1.1.0 on the Raspberry Pi 2
There is no official Kali support for the Raspberry Pi 2 with working images, and Kali 1.1.0 support, I wanted to find out if it was possible to get Kali 1.1.0 working on the latest Raspberry Pi 2 and the steps needed.
The Raspberry Pi 2 is small and low powered enough to be used as a penetration testing "drop box". It's a simple but fairly powerful device that can be inconspicuously plugged into a network and provide a penetration tester with the means to perform remote tests.
Specifications
Raspberry PI 2
The Raspberry PI 2 has significantly improved specifications compared to the Raspberry PI model B+, being approximately six times faster and having twice the memory.
The quick specifications are:-
900MHz quad core ARM Cortex-A7 CPU (~6x performance)
1GB RAM
4 port USB
10/100 Ethernet port.
Kali Linux 1.1.0
Kali Linux 1.1.0 was released on the 9/2/2015, and was described as a milestone release. With a new kernel patched for Wireless injection attacks, and improved wireless driver support.
Building a Kali Linux 1.10 image for the Raspberry Pi 2
A sample workflow would look similar to (armhf):
And slightly modified the workflow to the below:-
mkdir ~/arm-pi2
cd ~/arm-pi2
git clone https://github.com/offensive-security/gcc-arm-linux-gnueabihf-4.7
export PATH=${PATH}:/root/arm-pi2/gcc-arm-linux-gnueabihf-4.7/bin
git clone https://github.com/offensive-security/kali-arm-build-scripts
cd ~/arm-pi2/kali-arm-build-scripts
Then download the Raspberry Pi 2 kernel configuration, to the current folder (kali-arm-build-scripts) using the following command:-
wget http://pastebin.com/download.php?i=Rv3zpsiv -O pi2_kernel.config
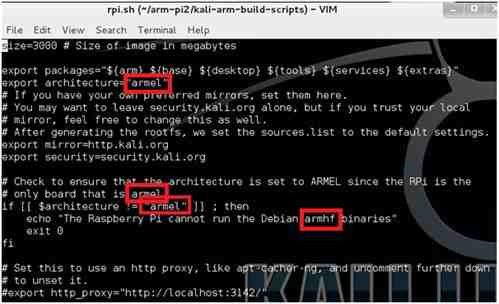
Then modify the rpi.sh script as below:-
And built the image using version 1.1.0 of Kali Linux:
./rpi.sh 1.1.0
For the next steps i am used a Windows laptop with a built in SD card reader, to write the created img to a high capacity SDHC card.
Extract the xz file to an img file using the Windows 7-zip program, and then use "Win32 Disk Imager" to write the img to the SDHC card.
The Linux equivalent would be to use the unxz utility to decompress the xz file, followed by a similar command:
- dd if=kali-1.1.0-rpi.img of=/dev/sdb bs=512k
Configuring Kali Linux on the Raspberry Pi 2.
Expanding the image to the size of the flash card
Insert the written SDHC card in the Raspberry Pi 2, and made the other necessary connections like attaching a keyboard/monitor/mouse and plugging a DHCP enabled network cable into the Raspberry Pi. And then powered the Raspberry Pi up, logging in using the default credentials root/toor:- (we suggest changing the password).
/scripts/rpi-wiggle.sh
However the sudo and parted programs were missing, so we had to use apt-get to install them:-
apt-get install sudo
apt-get install parted
Then the rpi-wiggle.sh program was able to run:-
/scripts/rpi-wiggle.sh
After this the Raspberry Pi will be reboot, Now ready for the full Kali build to be installed.
Installing the Full Kali Linux build
Now it is time to install the full Kali Linux build, by issuing the following commands:-
apt-get update
apt-get install kali-linux-full
After downloading and installing files, and answering a number of configuration screens, the installation will be completed and the command prompt will display:
Installing and configuring the SSH server
The next step is install and configure the SSH server. Though chkconfig first:
apt-get install chkconfigThen remove the run levels for SSH:
update-rc.d -f ssh removeAnd then load the SSH defaults to run level:
update-rc.d -f ssh defaultsNext, check that the SSH server was up and running:
chkconfig sshI suggest removing the default keys for the SSH server:
rm /etc/ssh/ssh_host_*Then create a new set of public and private keys:
dpkg-reconfigure openssh-serverNow restart the SSH server:
service ssh restart
You are done.
Note: I am used a SDHC for compatibility sake, which limited me to a maximum capacity of 32GB. Where possible select cards which have wear levelling, which distributes the writes across the memory, extending the life of the flash media. Finally i am used high speed media, selecting manufacturers from a published Raspberry Pi compatibility guide http://elinux.org/RPi_SD_cards
Use Android Device as Screen and Input for Raspberry Pi
Got an Android device? Want to use it as a screen and keyboard for Raspberry Pi? A simple trick described in a thread on the Raspberry Pi forum site can help you with that.
For this trick to work, you need an Android device that supports USB tethering and VX ConnectBot app installed on it.
1. Allows you to use your Android device as keyboard input and terminal display for your Raspberry Pi
2. Allows you to tether your Raspberry PI to your Android device's WiFi (3G untested, but should work).
- Your PI is configured to run SSHd on startup
- You are using the default Pi username / password
- Your Android device has internet connectivity via WiFi/3G and it is enabled
iface usb0 inet static address 192.168.42.42 netmask 255.255.255.0 network 192.168.42.0 broadcast 192.168.42.255This effectively turns the first USB port into a network interface. Reboot Raspbery Pi.
Now follow the steps:
1. Power down your Pi
2. Connect your Android device to your Pi via it's USB data cable
3. Power up your Pi... wait about a minute.
4. On your Android device, go to Settings / Wireless & Networks / More / Tethering & Portable Hotspot... click "USB tethering"
5. Start up VX ConnectBot and SSH "pi@192.168.42.42"
6. Keep hitting return until it asks you for your password. Enter it.
Congratulations - you should now have terminal access to your Pi with a software keyboard... kinda. Mine seems to disconnect the session every minute or so - very annoying.
Now to set up routing so that your Pi can see the world via your Android device.
7. Root yourself up
8. Check to see which IP address that your Android device is using
mine is 192.168.42.129
9. Add a default route pointing all traffic from your Pi out to your Android device. It's worth noting that this static route is temporary and will not survive rebooting your Pi. I've left it like this because I don't know if Android likes to change it's tether gateway address very often.
2. Connect your Android device to your Pi via it's USB data cable
3. Power up your Pi... wait about a minute.
4. On your Android device, go to Settings / Wireless & Networks / More / Tethering & Portable Hotspot... click "USB tethering"
5. Start up VX ConnectBot and SSH "pi@192.168.42.42"
6. Keep hitting return until it asks you for your password. Enter it.
Congratulations - you should now have terminal access to your Pi with a software keyboard... kinda. Mine seems to disconnect the session every minute or so - very annoying.
Now to set up routing so that your Pi can see the world via your Android device.
7. Root yourself up
mine is 192.168.42.129
9. Add a default route pointing all traffic from your Pi out to your Android device. It's worth noting that this static route is temporary and will not survive rebooting your Pi. I've left it like this because I don't know if Android likes to change it's tether gateway address very often.
If you've gotten this far, I'll assume you can figure out how to make a static route permanent if need be..
10. Test it!
10. Test it!
Top Android Apps For Advanced Usability With Raspberry Pi
Ever found yourself plugging a keyboard into your Raspberry Pi because you could be bothered to boot your PC to SSH, or found yourself desperately trying to remember the tiny computer’s IP address on your network?
There are a whole host of Android utilities that can be used by Raspberry Pi owners to make life easier, including a couple that are custom designed.
I have collected some of them together, all of which are free to install to Android phones and tablets.
Hacker’s Keyboard
The standard Android keyboard isn’t really any good for entering command line instructions (something you’ll probably need to do if connecting over SSH to your Raspberry Pi device) which is where the Hacker’s Keyboard comes in handy. Arguably more useful on devices with a larger screen or tablets, this app offers a standard keyboard layout for Android, with all of the characters — alpha-numeric and punctuation — where you would expect to find them.AndroidVNC
Rather than sending files by FTP or gaining command line access through SSH, what if you needed to setup a remote connection to the GUI in Raspbian or some other Pi distro?With a keyboard and a settings screen to manage how the mouse behaves and to send special keys (such as CTRL-ALT-DEL), AndroidVNC simplifies what might otherwise be a complicated mess of options. Not so great for smaller screens, AndroidVNC is perfect for phablets and tablets.
Fing
- You’ve just switched on your Raspberry Pi but you forgot to connect the HDMI lead, so you have no display. You don’t want to pull the plug, but you can’t ssh into it without the ip address. How to find it? Or…
- You got your headless Raspberry Pi up and running, but you forgot what ip address it’s on. Or…
- You rebooted your internet router and it’s changed the ip address of the Pi. What do you do?
Very useful indeed. There’s no looking back once you’ve got Fing installed. It’s a superb app. You can assign names to each device and choose an appropriate icon to make identification easier. They recently added a Raspberry Pi icon too…